我们生活在电脑可以被恶意软件感染的世界里。最着名的例子是WannaCry,它感染了世界不同国家的许多电脑。然而,还有许多其他恶意软件蠕虫在系统和目标计算机上执行。
You know that we are living in the world where PCs can be infected with malware. The best-known example is WannaCry which infected many computers in different countries of the world. However, there are many other malware worms which execute on a system and target computer running.

通常,恶意软件利用Microsoft Windows操作系统中的大多数情况下使用NTFS文件系统的漏洞。因此,我们想提供几个示例,数据提取器可以恢复作为恶意软件攻击目标的NTFS分区。
Usually, malware exploits a vulnerability in Microsoft Windows operation system where the NTFS file system is used in most cases. So we would like to give couple examples how Data Extractor can recover NTFS partition which was a target of malware attack.
最初很少有关于NTFS文件系统结构的理论。你可以在这里读到的基本细节。
Initially few theory about NTFS file system structure. Base details you can read here.
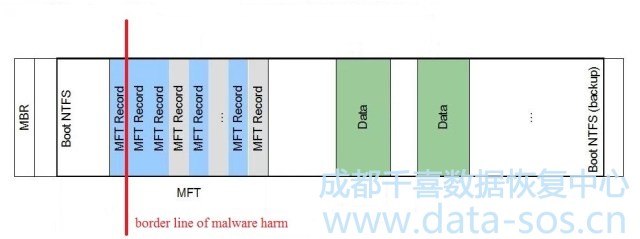
在我们的例子中,MBR、GPT表、主NTFS引导和几个MFT记录被擦除。
In our case, MBR, GPT table, main NTFS boot and several MFT records were erased.
但是,大多数NTFS分区和NTFS引导副本都没有受到损坏,并且可以像这里一样:
However, most of the NTFS partition and NTFS boot copy escape unharmed and can be imaged like here:
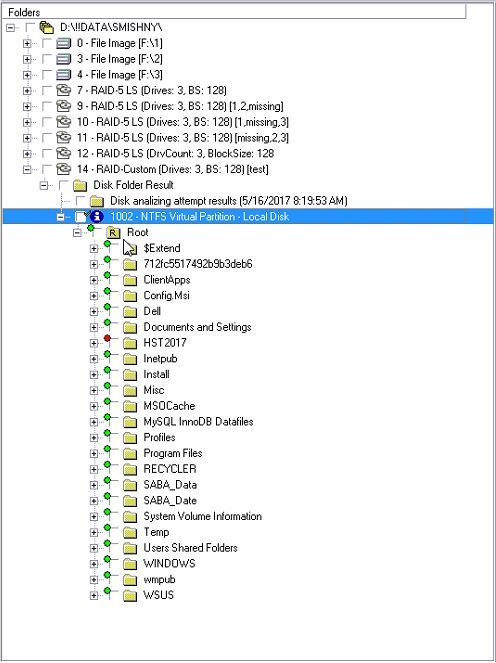
如果您是一个数据恢复专家,那么您就知道您可以使用引导副本来获得关于整个分区的实际信息。该选项适合这种情况,即“快速磁盘分析”,它在开始和结束时搜索文件系统结构,并尝试根据已发现的文件系统结构构建整个分区。
If you are a detective or data recovery specialist then you know that you can use boot copy to get actual information about the whole partition. The option is suited for this case is ‘Quick disk analysis’ which searches file system structures in the beginning and in the end of the drive and tries to build the whole partitions based on found file system structures.
在“快速磁盘分析”之后的结果如下:
The results after ‘Quick disk analysis’ option look like here:
我们现在正在处理数据提取器中的虚拟分区。现在我们可以恢复分区大部分的文件.但如果你是一名侦探或一名恶意软件研究员,你可能想要调查另一款软件的恶意软件行为。
We are working with the virtual partition in Data Extractor now. And we can recover most files of the partition right now. But if you are a detective or a malware researcher then you maybe want to investigate the evidence of malware actions by another software.
The main problem, in this case, is that you can’t open recovered NTFS partition without Data Extractor (boot is lost). PC-3000 Data Extractor allows to rebuild lost file system structures and you will be able to investigate the evidence of malware actions by another software.
There are two methods do that in Data Extractor:
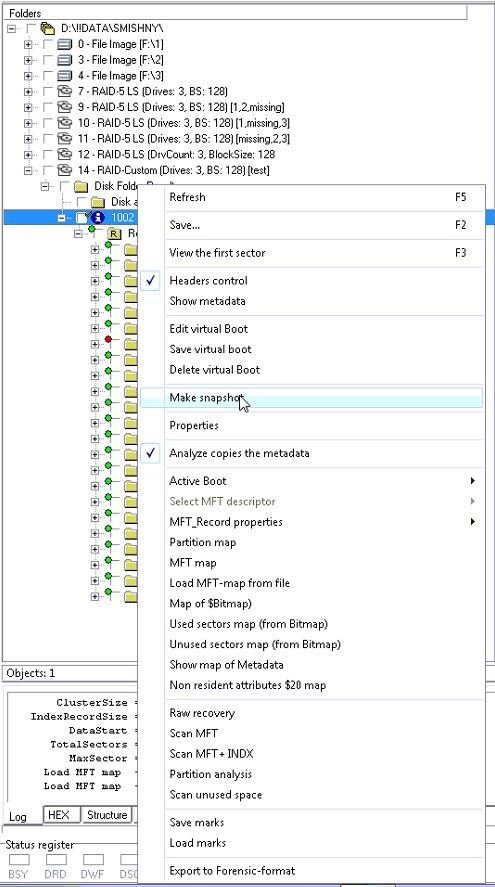
- 对找到的分区做一个快照。右键单击浏览器中的虚拟NTFS引导,并选择“快照”:
Make a snapshot of found partition. Right click on the virtual NTFS boot in Explorer and select ‘Make snapshot’:
该方法将扫描分区的所有条目:
This method scans all entries of the partition:
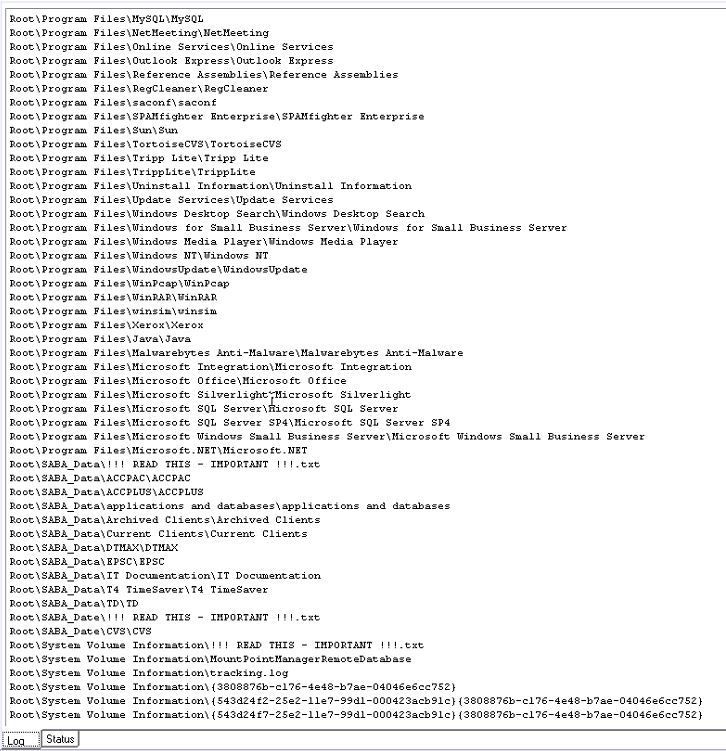
最后,创建另一个虚拟分区,它是初始的快照。
And finally, creates another virtual partition which is the snapshot of initial one.
This method has advantages and disadvantages. The main advantage is that you get all available files on this partition. Disadvantages are you can get list of files were on file system, not the filesystem (the snapshot doesn’t include data of sectors out of the file map) and maybe the main disadvantage – it can take a lot of time (just realize that you want to make snapshot of RAID array filesystem with several TB size).
第二种方法是为文件系统创建一个虚拟磁盘。在数据提取器中也有类似的虚拟机安装程序。您打开分区的映射:
2) The second method is to create a virtual disk for the filesystem. It’s similar procedure of virtual machine mounting in Data Extractor. You open map of the partition:
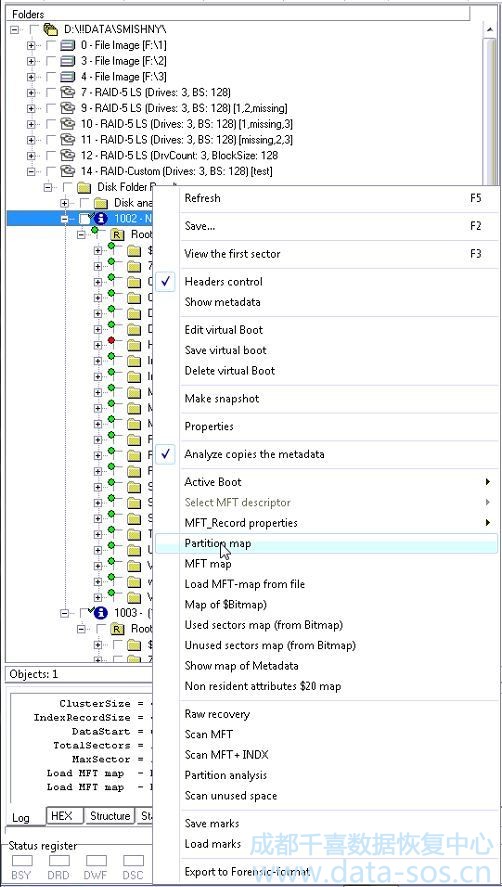
我们获取分区的映射,并尝试验证主引导是否可用(从引导副本中恢复):
We get the map of partition and can try to verify that main boot is available now (it was recovered from boot copy):
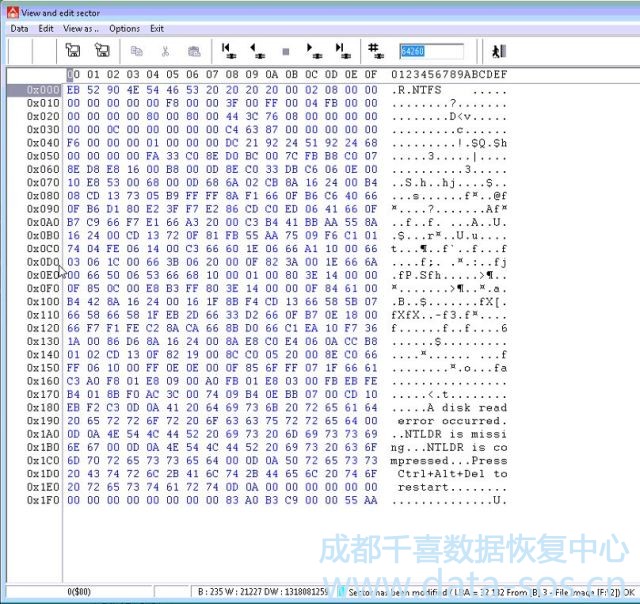
It’s here!!! Pay attention to the note that sector was modified. (All modifications are performed with copy of the data and you will not lose an evidence of malware actions).
下一步是将分区映射挂到虚拟磁盘:
Next step is to mount the map of partition into virtual disk:
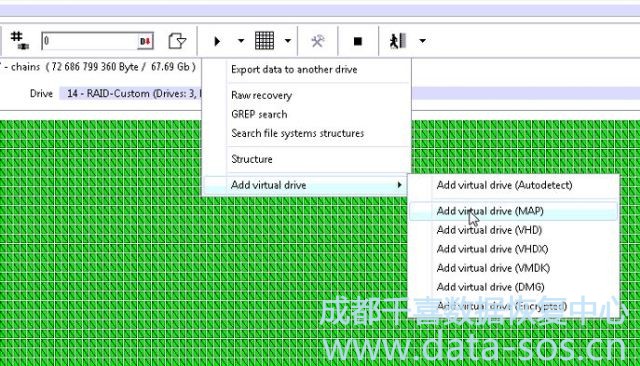
And we get the solid disk.
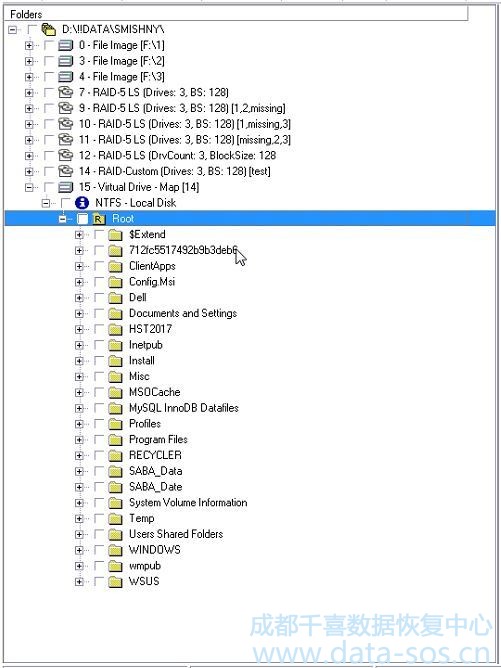
我们可以将其安装在操作系统中,或者将其提取到另一个驱动器上以进一步调查。
We can mount it in the operation system or extract on another drive to further investigation now